One Note the Authentication Session Has Expired Please Signin Again
This browser is no longer supported.
Upgrade to Microsoft Border to take advantage of the latest features, security updates, and technical support.
Configure hallmark session direction with Conditional Access
In complex deployments, organizations might have a demand to restrict authentication sessions. Some scenarios might include:
- Resource access from an unmanaged or shared device
- Access to sensitive information from an external network
- High impact users
- Critical business organization applications
Provisional Access controls allow y'all to create policies that target specific use cases within your organization without affecting all users.
Before diving into details on how to configure the policy, let'southward examine the default configuration.
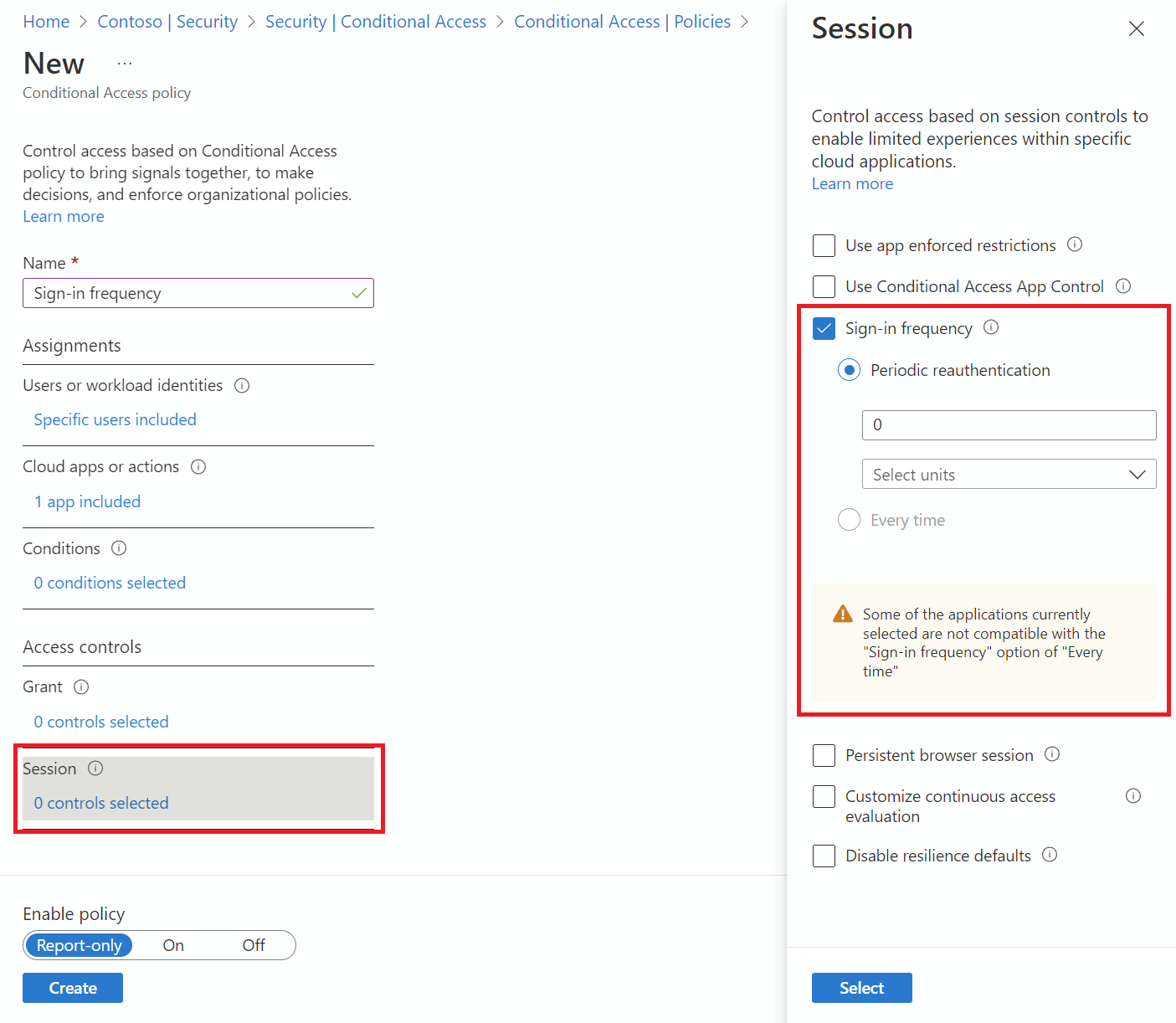
User sign-in frequency
Sign-in frequency defines the time period before a user is asked to sign in again when attempting to access a resource.
The Azure Agile Directory (Azure Ad) default configuration for user sign-in frequency is a rolling window of 90 days. Asking users for credentials often seems similar a sensible affair to do, but it tin can backfire: users that are trained to enter their credentials without thinking can unintentionally supply them to a malicious credential prompt.
It might sound alarming to not ask for a user to sign back in, in reality whatever violation of It policies volition revoke the session. Some examples include (but aren't limited to) a password alter, an incompliant device, or account disable. You tin can too explicitly revoke users' sessions using PowerShell. The Azure Advertising default configuration comes down to "don't ask users to provide their credentials if security posture of their sessions hasn't changed".
The sign-in frequency setting works with apps that take implemented OAUTH2 or OIDC protocols according to the standards. Most Microsoft native apps for Windows, Mac, and Mobile including the following web applications comply with the setting.
- Give-and-take, Excel, PowerPoint Online
- OneNote Online
- Office.com
- Microsoft 365 Admin portal
- Exchange Online
- SharePoint and OneDrive
- Teams web client
- Dynamics CRM Online
- Azure portal
The sign-in frequency setting works with SAML applications as well, as long as they don't drop their own cookies and are redirected back to Azure AD for hallmark on regular footing.
User sign-in frequency and multi-factor authentication
Sign-in frequency previously applied to only to the first factor authentication on devices that were Azure Ad joined, Hybrid Azure Ad joined, and Azure AD registered. There was no easy mode for our customers to re-enforce multi gene hallmark (MFA) on those devices. Based on customer feedback, sign-in frequency will apply for MFA likewise.

User sign-in frequency and device identities
If you take Azure Advertizing joined, hybrid Azure Advertisement joined, or Azure Advertising registered devices, when a user unlocks their device or signs in interactively, this result will satisfy the sign-in frequency policy every bit well. In the following two examples user sign-in frequency is set to one hour:
Case 1:
- At 00:00, a user signs in to their Windows 10 Azure Advert joined device and starts piece of work on a document stored on SharePoint Online.
- The user continues working on the same document on their device for an 60 minutes.
- At 01:00, the user is prompted to sign in again based on the sign-in frequency requirement in the Conditional Access policy configured past their administrator.
Example 2:
- At 00:00, a user signs in to their Windows 10 Azure Advertising joined device and starts work on a document stored on SharePoint Online.
- At 00:30, the user gets up and takes a break locking their device.
- At 00:45, the user returns from their interruption and unlocks the device.
- At 01:45, the user is prompted to sign in once more based on the sign-in frequency requirement in the Conditional Access policy configured by their administrator since the last sign-in happened at 00:45.
Require reauthentication every time (preview)
At that place are scenarios where customers may desire to require a fresh authentication, every time before a user performs specific actions. Sign-in frequency has a new selection for Every time in improver to hours or days.
The public preview supports the following scenarios:
- Crave user reauthentication during Intune device enrollment, regardless of their current MFA status.
- Require user reauthentication for risky users with the require password alter grant control.
- Require user reauthentication for risky sign-ins with the require multi-factor hallmark grant control.
When administrators select Every fourth dimension, it will require full reauthentication when the session is evaluated.
Annotation
An early preview version included the option to prompt for Secondary authentication methods just at reauthentication. This pick is no longer supported and should not be used.
Persistence of browsing sessions
A persistent browser session allows users to remain signed in after closing and reopening their browser window.
The Azure Advertizement default for browser session persistence allows users on personal devices to choose whether to persist the session past showing a "Stay signed in?" prompt subsequently successful hallmark. If browser persistence is configured in AD FS using the guidance in the commodity AD FS Single Sign-On Settings, we'll comply with that policy and persist the Azure AD session every bit well. You can also configure whether users in your tenant see the "Stay signed in?" prompt past changing the appropriate setting in the company branding pane in Azure portal using the guidance in the article Customize your Azure AD sign-in page.
Configuring authentication session controls
Conditional Admission is an Azure AD Premium adequacy and requires a premium license. If you would like to learn more about Conditional Access, meet What is Conditional Admission in Azure Active Directory?
Warning
If y'all are using the configurable token lifetime characteristic currently in public preview, please note that we don't back up creating 2 unlike policies for the aforementioned user or app combination: i with this feature and another ane with configurable token lifetime characteristic. Microsoft retired the configurable token lifetime feature for refresh and session token lifetimes on Jan thirty, 2021 and replaced it with the Conditional Access hallmark session management feature.
Before enabling Sign-in Frequency, make sure other reauthentication settings are disabled in your tenant. If "Remember MFA on trusted devices" is enabled, be sure to disable information technology before using Sign-in frequency, as using these 2 settings together may lead to prompting users unexpectedly. To learn more most reauthentication prompts and session lifetime, see the commodity, Optimize reauthentication prompts and understand session lifetime for Azure Advert Multi-Factor Authentication.
Policy deployment
To make sure that your policy works as expected, the recommended best practice is to exam it before rolling it out into product. Ideally, employ a test tenant to verify whether your new policy works as intended. For more than data, see the article Plan a Provisional Admission deployment.
Policy 1: Sign-in frequency control
-
Sign in to the Azure portal as a global administrator, security ambassador, or Conditional Access administrator.
-
Scan to Azure Agile Directory > Security > Conditional Access.
-
Select New policy.
-
Requite your policy a name. Nosotros recommend that organizations create a meaningful standard for the names of their policies.
-
Cull all required conditions for client'southward environment, including the target deject apps.
Note
It is recommended to set equal hallmark prompt frequency for key Microsoft Office apps such as Exchange Online and SharePoint Online for all-time user feel.
-
Under Access controls > Session.
- Select Sign-in frequency.
- Enter the required value of days or hours in the first text box.
- Select a value of Hours or Days from dropdown.
-
Save your policy.
On Azure AD registered Windows devices, sign in to the device is considered a prompt. For example, if you've configured the sign-in frequency to 24 hours for Function apps, users on Azure Advertizing registered Windows devices will satisfy the sign-in frequency policy past signing in to the device and will be not prompted again when opening Part apps.
Policy 2: Persistent browser session
-
Sign in to the Azure portal every bit a global administrator, security administrator, or Conditional Access administrator.
-
Browse to Azure Active Directory > Security > Provisional Access.
-
Select New policy.
-
Give your policy a name. We recommend that organizations create a meaningful standard for the names of their policies.
-
Choose all required atmospheric condition.
Note
Delight note that this command requires to choose "All Cloud Apps" as a condition. Browser session persistence is controlled past authentication session token. All tabs in a browser session share a single session token and therefore they all must share persistence state.
-
Under Access controls > Session.
- Select Persistent browser session.
- Select a value from dropdown.
-
Save your policy.

Note
Persistent Browser Session configuration in Azure AD Conditional Access volition overwrite the "Stay signed in?" setting in the visitor branding pane in the Azure portal for the same user if you have configured both policies.
Policy three: Sign-in frequency command every time risky user
- Sign in to the Azure portal as a global administrator, security administrator, or Conditional Admission administrator.
- Scan to Azure Active Directory > Security > Conditional Access.
- Select New policy.
- Give your policy a name. We recommend that organizations create a meaningful standard for the names of their policies.
- Nether Assignments, select Users and groups.
- Under Include, select All users.
- Under Exclude, select Users and groups and cull your organization's emergency access or interruption-glass accounts.
- Select Done.
- Under Cloud apps or actions > Include, select All cloud apps.
- Under Conditions > User risk, set Configure to Aye. Nether Configure user gamble levels needed for policy to exist enforced select High, then select Done.
- Under Access controls > Grant, select Grant access, Require password change, and select Select.
- Under Session controls > Sign-in frequency, select Every fourth dimension (preview).
- Confirm your settings and set Enable policy to Study-only.
- Select Create to create to enable your policy.
After administrators ostend your settings using report-simply mode, they can move the Enable policy toggle from Study-only to On.
Validation
Use the What-If tool to simulate a login from the user to the target application and other weather condition based on how you configured your policy. The authentication session direction controls testify up in the outcome of the tool.

Prompt tolerance
We cistron for 5 minutes of clock skew, so that we don't prompt users more often than in one case every five minutes. If the user has done MFA in the concluding five minutes, and they hit another Conditional Access policy that requires reauthentication, we won't prompt the user. Over-promoting users for reauthentication tin impact their productivity and increment the run a risk of users approval MFA requests they didn't initiate. We highly recommend using "Sign-in frequency – every fourth dimension" only for specific business organization needs.
Known issues
- If you configure sign-in frequency for mobile devices, authentication subsequently each sign-in frequency interval could be deadening (information technology tin can take 30 seconds on average). Also, it could happen beyond various apps at the same fourth dimension.
- In iOS devices, if an app configures certificates as the first hallmark factor and the app has both Sign-in frequency and Intune mobile application management policies applied, the end-users volition be blocked from signing in to the app when the policy is triggered.
Next steps
- If you're gear up to configure Conditional Admission policies for your environment, see the article Programme a Provisional Access deployment.
Feedback
Submit and view feedback for
Source: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-session-lifetime
0 Response to "One Note the Authentication Session Has Expired Please Signin Again"
Post a Comment